evolutionQ Warns of Quantum Deadline for Global Cryptographic Security
A leading quantum security pioneer warns that without swift adoption of layered defenses, critical infrastructure could face catastrophic disruptions
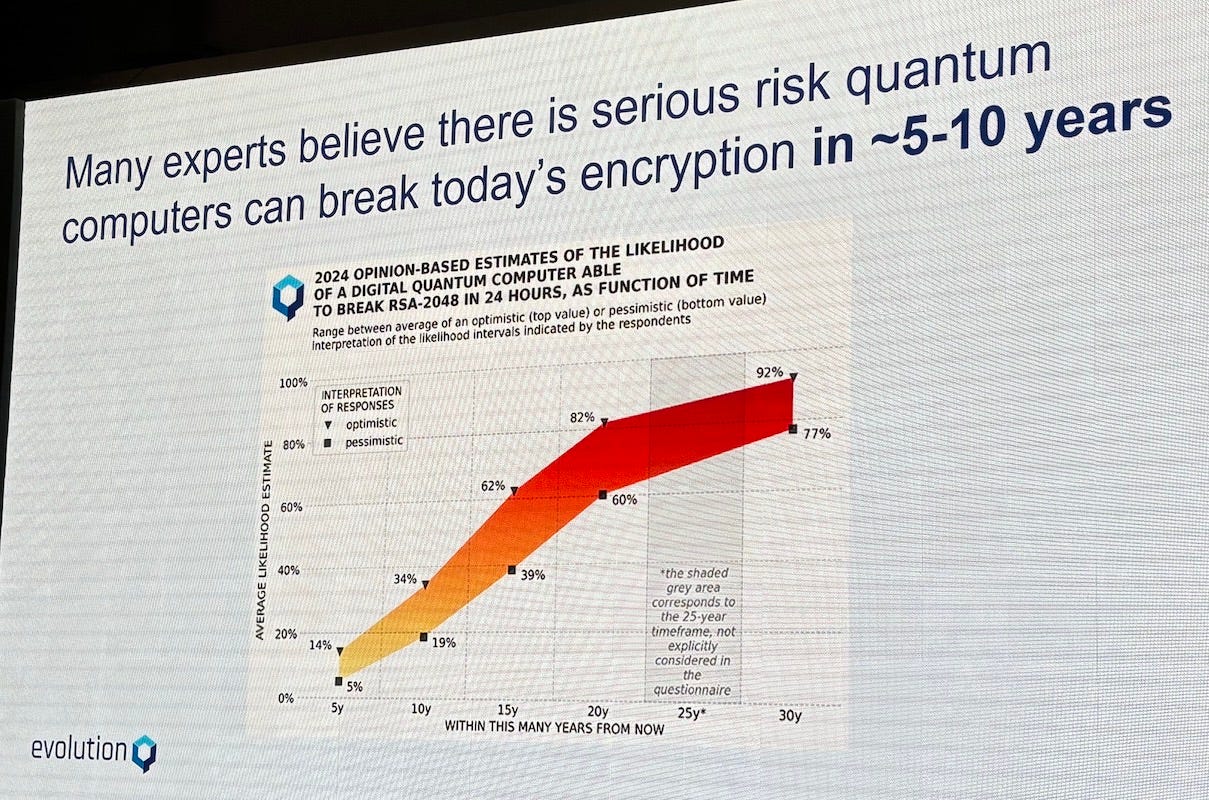
The quantum threat to current cryptographic systems has shifted from a hypothetical concern to an operational priority. For nearly three decades, cybersecurity experts have cautioned that public key infrastructure—once the backbone of internet security—will be rendered obsolete by quantum algorithms capable of breaking it in hours or minutes. Those warnings are no longer theoretical. The probability of a systemic breach within the next five years now sits between 5% and 14%, a range that some specialists believe is conservative.
While much public commentary frames the issue as a battle between state intelligence agencies, the more pressing danger is the systemic collapse of civilian systems.
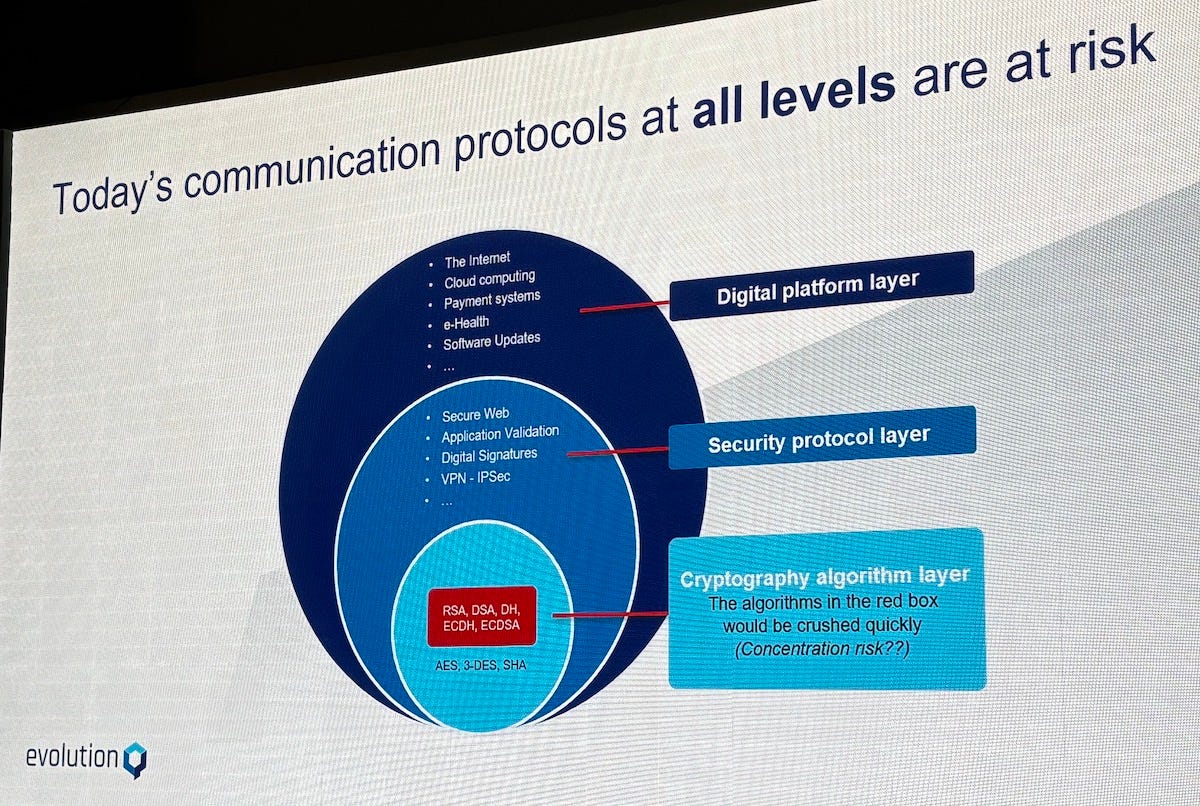
Cryptography is the invisible foundation of everyday life: securing hospital records, cloud computing platforms, banking transactions, transportation logistics, energy grids, and food supply chains. If public key cryptography were suddenly broken, these systems could fail without any credible, rapid remediation strategy, leaving governments and enterprises struggling to restore even basic operations.
“You don’t know when a burglar is going to break into your house. You still lock the door,” said Michele Mosca, co-founder and chief executive of evolutionQ, stressing that risk tolerance, not an exact “Q Day” forecast, should drive decision-making.
The longstanding “record now, decrypt later” scenario—where adversaries harvest encrypted data now for future decryption—has already been observed. In the quantum context, this risk is magnified because the migration to quantum-safe systems can take years, and the window for completing it is closing.
The industry’s slow progress is partly due to what Mosca called “crypto procrastination”—the habit of delaying security overhauls because the precise arrival date of the threat is unknown. Yet even a 10% chance of missing the migration deadline is unacceptable when the outcome could mean more than the loss of state secrets: it could be the loss of functioning economies and public trust in digital systems.
Momentum is finally building. Standards bodies such as the U.S. National Institute of Standards and Technology (NIST) and the European Telecommunications Standards Institute (ETSI) have developed usable post-quantum cryptography (PQC) standards. Meanwhile, industry leaders are coordinating with vendors to begin phased migration.
“Pick a date,” Mosca urged, warning that endless speculation about Q Day simply delays action and prevents ecosystems from organising around a clear deadline.
Addressing Systemic Risk
Mosca emphasised that the central challenge is not technological capability but governance. Risk oversight frameworks that scrutinise supplier dependencies often fail to recognise that nearly all critical systems depend on the same handful of cryptographic algorithms. This creates a dangerous concentration risk that is rarely addressed in corporate or governmental risk assessments.
True resilience requires agility—the ability to recover from a cryptographic compromise in a timeframe appropriate to the risk. Agility is not achieved by sprinkling “quick fixes” on top of legacy systems; it must be designed into security architectures from the start. Defense-in-depth principles, which have been used for decades in other domains, should also be applied to cryptography, as they are in authentication via multi-factor authentication.
In the 1990s, public key infrastructure was the right solution for scaling internet security. Today, Mosca argues, symmetric key infrastructure offers the most promising path toward scalable resilience. State actors and central banks have long relied on pre-shared keys in conjunction with symmetric cryptography. The challenge is scaling such models to the civilian critical infrastructure that underpins modern economies.
Beyond the PQC vs. QKD Divide
The long-running debate between proponents of post-quantum cryptography and those advocating for quantum key distribution (QKD) is, in Mosca’s view, unhelpful.
“We need to migrate to post-quantum public key cryptography ASAP,” he said, “and we need more scalable ways to achieve that extra layer of assurance.”
Rather than treating the two as mutually exclusive, organisations should integrate both into layered strategies, he added.
Encouragingly, the ecosystem is diversifying. Multiple companies are now delivering scalable pre-shared and symmetric key solutions, while others continue to advance quantum cryptography.
evolutionQ has positioned itself within this ecosystem as an early mover with deep technical expertise, a history of thought leadership, and a practical, implementation-first approach. By producing tangible tools—such as a standardized list of eight key questions that organizations should ask their vendors—Mosca’s firm bridges the gap between technical readiness and real-world adoption.
Unlike newer entrants to the quantum security market, evolutionQ’s credibility rests on its decades-long track record of advocating for quantum-safe transitions before they became mainstream. The firm’s work extends beyond product delivery to ecosystem coordination, helping industries establish realistic timelines and fostering collaboration between vendors and end-users. This emphasis on readiness and interoperability distinguishes evolutionQ from firms that focus solely on developing proprietary cryptographic products.
Mosca also cautioned against complacency in evaluating new cryptographic algorithms. Two NIST finalist candidates were broken by researchers in less than a weekend, demonstrating that algorithmic security is a moving target. Breakthroughs can emerge unexpectedly, aided by artificial intelligence and eventually by quantum-enhanced cryptanalysis.
Treating algorithms as permanent solutions, rather than components in an evolving defense posture, risks repeating the vulnerabilities of today’s systems, he said.
Parallel Actions for Resilience
A common excuse for inaction, Mosca said, is that organisations have not completed their cryptographic inventories. While knowing the exact state of a network’s encryption is valuable, waiting to act until such inventories are perfect is a strategic mistake.
Instead, organisations should start with top-down risk assessments to identify the most dangerous “rotting corpses” in their cryptographic landscape—such as outdated SSL/TLS implementations, unpatched VPN gateways, and legacy IoT devices—and remove them immediately, while building and maintaining detailed inventories in parallel.
Practical steps include communicating with vendors and third-party partners to ensure they are aligned on quantum-safe timelines and requirements. evolutionQ’s vendor engagement framework, combined with its advisory role in multiple standards bodies and industry forums, enables it to accelerate readiness across entire supply chains.
The goal is to move from isolated organisational preparedness to ecosystem-wide resilience—an approach that Mosca believes is essential to mitigating systemic risk.
Looking ahead, Mosca believes the conversation will soon change from “Why should we do this?” to “Why haven’t you done this yet?”—a transformation he has seen before in other security domains.
He said the ultimate goal is to enable society to fully leverage the opportunities of quantum computing and artificial intelligence without compromising the cryptographic systems that underpin them.
“We want to boldly and assertively embrace all the positive value creation capabilities of quantum computing and AI, without realizing too late that they’ve broken the public key cryptography underpinning our economy,” he concluded.
Achieving that vision will require not only swift adoption of PQC but also diversification of cryptographic methods, investment in resilience, and a cultural shift in risk governance.
The quantum era will not wait for slow adopters. By embedding resilience at every layer of critical infrastructure, and by treating cryptography as a living system rather than a fixed asset, organisations can prepare for the inevitable challenges ahead—and ensure that preventable crises do not overshadow the benefits of quantum innovation.